- Friday
- May 10th, 2024
- Share Files
Get Complete Project Material File(s) Now! » Global Authentication and Incremental Cryptography Global authenticity is a strong security notion that aims at protecting all the local tags from tampering. A simple solution is to store all these tags in persistent...
Get Complete Project Material File(s) Now! » What is Internet of Things (IoT) In 1999, Kevin Ashton of Procter & Gamble tabled the term “Internet of Things for the very first time. In simple words, the Internet of Things (IoT)...
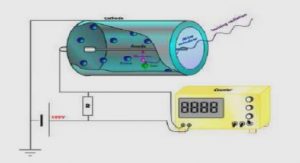
Get Complete Project Material File(s) Now! » Micro-robotics, observation and actuation The driving forces behind micro-scale experimentation hang on appropriate observation, actuation and control tools which are the centrepiece of micro-robotics. Micro-robotics as a field has been developed since the...

Get Complete Project Material File(s) Now! » Update Serializability (US) Update serializability, introduced by Garcia-Molina and Wiederhold [57], guarantees that update transactions are serialized with respect to other update transactions. Read-only transactions only need to take consistent snapshots, and always...

Get Complete Project Material File(s) Now! » Outsourced data Confidentiality by Encryption Despite that traditional encryption mechanisms (e.g., Data Encryption Standard (DES) [NIST 1999] and Advanced Encryption Standard (AES) [FIPS. 2001]) ensures strong confidentiality guarantees. They are suffering from two...

Get Complete Project Material File(s) Now! » Outsourced data Confidentiality by Encryption Despite that traditional encryption mechanisms (e.g., Data Encryption Standard (DES) [NIST 1999] and Advanced Encryption Standard (AES) [FIPS. 2001]) ensures strong confidentiality guarantees. They are suffering from two...

Get Complete Project Material File(s) Now! » A brief historical overview of speech processing and privacy Speech processing came a long way since 1881 when the earliest device for recording speech was invented by Alexander Graham Bell. It used a...

Get Complete Project Material File(s) Now! » Secure storage and secure computation Three main functions are required to protect digital data during its life cycle: secure storage, secure computing and secure sharing. One of the most promising method for securing...

Get Complete Project Material File(s) Now! » Data Concepts and Notation Different terminology is applied in different works; for instance, fragments are sometimes called chunks, shards, or shares. The following data concepts, notation, and terminology are introduced in order to...

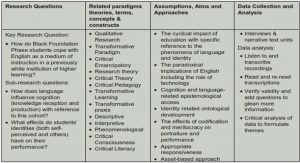
Get Complete Project Material File(s) Now! » Theoretical framework This section covers the theoretical framework of this thesis. In the literature review the main themes were established: Origins of IoT, enabling trends and technologies, transformational potential, communication models and challenges...
