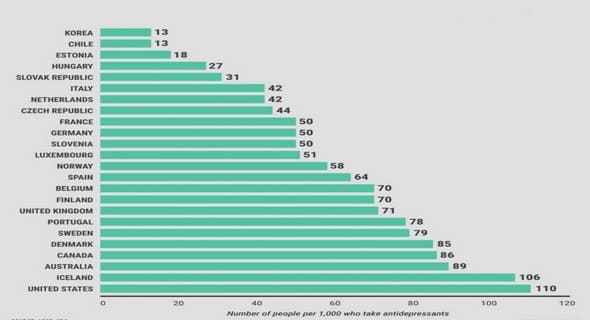
(Downloads - 0)
For more info about our services contact : help@bestpfe.com
Table of contents
1 General Introduction
2 Preliminaries
2.1 Mathematical Notation
2.2 Algorithm
2.3 Provable Security
2.4 Computational Assumptions
2.4.1 Group-Family Generators
2.4.2 Assumptions on Public-Order-Group Generators
Discrete-Logarithm Assumption
Relation Assumptions
2.4.6 Pairing-Group Structures
Assumptions
2.4.7 Assumptions on Hidden-Order-Group Generators
2.5 Cryptographic Primivites
2.5.1 Public-Key Encryption
2.5.2 Digital Signatures
2.5.3 Non-Interactive Commitments
Extractable Commitments
2.6 Zero-Knowledge Arguments
2.6.1 Interactive Systems
Schnorr Proofs
Interactive Arguments in the Random–Oracle Model
Fiat–Shamir Heuristic
2.6.2 Non-Interactive Systems
I Group Signatures and Protocols for Message Confidentiality
3 Introduction
3.1 Group Signatures
3.2 Vehicle-to-Vehicle Communication
3.3 Hardware Security without Secure Hardware
3.4 Results
3.4.1 Group Signatures
3.4.2 Vehicle-to-Vehicle Communication
3.4.3 Encryption with Password-Protected Assisted Decryption
4 Short Threshold Dynamic Group Signatures
4.1 Preliminaries
4.1.1 Hardness Assumptions
4.1.5 Pointcheval–Sanders Signature Scheme
4.1.6 Multi-Signatures with Key Aggregation
Syntax
Security Model
4.1.7 Generalized Forking Lemma
4.2 Threshold Dynamic Group Signatures
4.2.1 Syntax
Correctness
4.2.2 Security Model
Global Variables
Oracles
Anonymity
Traceability
On Non-Frameability
4.3 Main Construction
4.3.1 Variant of the PS Signature Scheme
4.3.2 Construction with Separate Issuers and Openers
Scheme Description
Discussion
Efficiency
Comparison with other Schemes
4.4 Threshold Group Signatures without Ledger
4.5 Pointcheval–Sanders Multi-Signatures
4.6 Distributed Group Signatures from Multi-Signatures
4.6.1 Construction Security
5 Zone Encryption with Anonymous Authentication
5.1 Preliminaries
5.1.1 Deterministic Authenticated Encryption
Security Properties
SIV Construction
5.2 Group Signatures with Attributes
5.2.1 Definition
Syntax
Correctness & Security Properties
5.2.2 Construction of Group Signatures with Attributes
Efficiency
Threshold Group Signatures with Attributes
5.3 Zone Encryption
5.3.1 Syntax of Zone Encryption Schemes
5.3.2 Security of Zone Encryption Schemes
Common Oracles
Payload Hiding
Anonymity
Traceability
Ciphertext Integrity
Zone Encryption with Multiple Authorities
5.3.7 Construction of a Zone-Encryption Scheme
Formal Description
Correctness & Security
5.3.13 Efficiency & Comparison
Efficiency
C-ITS Deployment and Comparison
5.3.14 Threat Model and Design Choices
5.3.15 Deployment Challenges
6 Hardware Security without Secure Hardware: How to Decrypt with a Password and a Server
6.1 Preliminaries
6.1.1 Hardness Assumptions
6.1.3 Signatures
6.1.4 Groth’s Strong One-Time Signatures
6.1.5 Jutla and Roy’s Signature Scheme
6.1.6 Public-Key Encryption
6.1.7 Smooth Projective Hash Functions
6.1.8 Key-Derivation Functions
6.2 Malleable Non-Interactive Proofs
6.2.1 Transformations
6.2.2 Simulation Soundness under Controlled Malleability
Formal Definition
6.2.3 Generic Construction
6.2.4 Strong Derivation Privacy
6.2.5 Groth–Sahai Proofs
Instantiation under the SXDH Assumption
6.3 Model for Password-Assisted Decryption
6.3.1 Syntax
6.3.2 Security Definitions
P-IND-RCCA Security
Blindness
Verifiability
6.4 Construction
6.4.1 Verification of Blinded Ciphertexts
Formal Description
6.4.2 Main Construction
Construction Overview
Formal Description
Correctness & Security
Efficiency
On Adaptive Corruptions
On Composability
Mitigating Server Breaches
7 Conclusion and Future Work
7.1 Conclusion
7.2 Future Work
II Zero-Knowledge Arguments and Randomness Certification
8 Introduction
8.1 Diophantine Satisfiability
8.1.1 Prior Work
8.2 Public-Key Generation with Verifiable Randomness
8.2.1 Related Work
8.3 Results
8.3.1 Diophantine Satisfiability
8.3.2 Public-Key Generation with Verifiable Randomness
9 Succinct Diophantine-Satisfiability Arguments
9.1 Preliminaries
9.1.1 Non-interactive Commitments in the Random-Oracle
Model
9.2 Integer Commitments
9.2.1 Damgård–Fujisaki Commitments
9.2.2 A new Integer-Commitment Scheme
Correctness & Security
Argument System FS.H
Arguing Knowledge of Openings
Multi-Integer Commitments
9.3 Succinct Inner-Product Arguments on Integers
9.3.1 Formal Description
Relations
Main Insights
Protocol Algorithms
Prover-Communication Complexity
Verification via a Single Multi-Exponentiation
Ultimate Commitment
Expression for g and h
Verification Efficiency
9.3.3 Completeness and Security
Challenge-Tree Generators
9.4 Succinct Arguments for Multi-Integer Commitments
9.4.1 Succinct Arguments of Openings
9.4.2 Aggregating Arguments of Openings to Integer Commitments
Protocol
Completeness and Security
9.4.3 Shorter Parameters for Integer Commitments
9.4.4 Succinct Base-Switching Arguments
9.5 Succinct Argument for Diophantine Equations
9.5.1 Arguments via Polynomial-Degree Reductions
Reducing Arbitrary Polynomials to Polynomials of Degree at most
Diophantine Equations as Circuits
9.5.2 Protocol
Main Insights
Protocol Algorithms
Prover-Communication Complexity
Verification Effiency
9.5.3 Completeness and Security
9.6 Applications
9.6.1 Arguing Knowledge of RSA signatures
9.6.2 Argument of Knowledge of (EC)DSA Signatures
DSA Signatures
ECDSA Signatures
9.6.3 Argument of Knowledge of List Permutation
9.6.4 3-SAT Satisfiability Argument
9.6.5 Integer-Linear-Programming Satisfiability Argument
10 Public-Key Generation with Verifiable Randomness
10.1 Preliminaries
10.1.1 Randomness Sources and Min-Entropy
10.1.2 Randomness Extractors
10.1.3 Universal Computational Extractors
Pseudo-Random Functions
Dodis–Yampolskiy Pseudo-Random Function
10.1.4 Chernoff’s Bound
10.2 Model for Key Generation with Verifiable Randomness
10.2.1 Syntax
10.2.3 Security Oracles
10.3 Generic Constructions
10.3.1 Key-Generation Protocol with Verifiable Randomness
for Probabilistic Circuits
Probabilistic Circuits
Generic Protocol
Discrete-Logarithm Keys
10.3.4 RSA-Key Generation Protocol with Verifiable Randomness Protocol
10.4 Instantiation of the RSA-Key Generation Protocol
10.4.1 Zero-Knowledge Argument with the Dodis–Yampolskiy
PRF Proof Strategy
10.4.2 Logarithmic-Size Argument of Double Discrete Logarithm
10.4.3 Logarithmic-Size Argument of Discrete-Logarithm Equality in two Groups
10.4.4 An Intermediate Protocol in G2
10.4.5 Protocol for R0
Security
Efficiency
Total Proof Size
Running Time
Overall Communication Size