Get Complete Project Material File(s) Now! »
Government Policies, Strategies and Standards
In 2010 the government of Rwanda unveiled the National Information and Communication Infrastructure (NICI) 2010 plan (Government of Rwanda, 2010). With regards to eGovernment, the plan aims to ensure that that implementation cuts across ministries and agencies horizontally so that complete business processes are automated and not just departmental planned actions. Furthermore it is planned that core design criteria for eGovernment applications in terms of portal design, look and feel, and minimal content will be identified and standardized. Another point of interest is the identification of re-usable applications and ensuring that duplication does not take place, together with implementation of standardized data dictionaries and controlled data exchange to ensure proper ownership of information.
Legal Environment
The following legislation in Rwanda is related to information security in e-Government: a) The Constitution of the Republic of Rwanda (Republic of Rwanda, 2003) in Article 22 states that : “The private life, family, home or correspondence of a person shall not be subjected to arbitrary interference; his or her honour and good reputation shall be respected. A person’s home is inviolable. No search of or entry into a home may be carried out without the consent of the owner, except in circumstances and in accordance with procedures determined by law. Confidentiality of correspondence and communication shall not be subject to waiver except in circumstances and in accordance with procedures determined by law.”
Resources
Tanzania is a country in East Africa with a population of about 43 million people and per capita GDP in 2009 of Tanzania Shillings 693,185 or USD 522 (Ministry of Finance and Economic Affairs – Tanzania, 2010a). The government of Tanzania consists of central government ministries, departments and government agencies or parastatal organizations. The central government budget for the financial year 2010/2011 by the Ministry of Communication, Science & Technology, which is responsible for ICT, was Tanzania Shillings 3.1billion – equivalent to about USD 2million (Ministry of Finance and Economic Affairs – Tanzania, 2010b). Internet penetration stands at 11% of the population (Tanzania Communications Regulatory Authority, 2010). A shortage of ICT skills in central and local government in Tanzania has been documented in research carried out by Msuya (2010).
e-Government Implementations
Examples of e-Government implementations that have been carried out were obtained from interviews with staff of MDAs as well as requests for information from an online discussion group of Tanzanian IT professionals. This forum is called ethinktank Tanzania and is accessible at the URL http://groups.yahoo.com/group/eThinkTankTz/. The list below gives a description of four e-Government implementations. a) Parliamentary Online Information System (POLIS) POLIS is an open access system implemented in 2003. The system provides an index to the proceedings and publications of the Parliament of Tanzania and it includes the full text of parliamentary motions.
National Cultural Considerations
A national ICT master plan and e-Government network feasibility study carried out in Uganda in 2006 (MEGA-TECH, Inc, 2006) states the following: “There is a broad range of individual, and largely uncoordinated, ICT initiatives and programs ongoing across the Government. This lack of coordination precludes a planned, managed, and adequately funded integrated approach to ICT development. Therefore, an ICT Master Plan to guide the coherent development of ICT within the government must focus on structures and processes that foster integration, 73 cooperation, and common objectives and processes. Even successful ICT initiatives such as the World Bank project with the Ministry of Finance to implement the Financial Management System and the Information Sharing System have not resulted in a dialogue of lessons learned with other Government entities to provide a model of ICT implementation.”
Presence of an information security policy
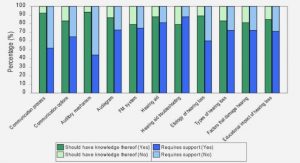
The East African Regional e-Government Strategy, (East African Community Secretariat, 2005) states that the EAC shall develop a secure information infrastructure in all the partner states. By implication, all participating MDAs shall have to have secure information infrastructures in place both for internal and for G2G transactions. An organizational information security policy is a tool that is useful in documenting the information security guidelines that need to be adhered to be an organization. Such a document would typically incorporate the particular contextual issues that are relevant to the organization and is usually aligned with the organizations operational activities and strategic goals. An organizational information security policy should guide both internal organizational transaction and external collaborations. For the purpose of this survey, a question was asked as to whether or not an information security policy was in place.
Table of Contents :
- PART I: INTRODUCTION
- Chapter 1 Introduction and Background
- 1.1 Introduction
- 1.2 Background
- 1.3 Motivation of the Study
- 1.4 Problem Statement
- 1.5 Objectives of the Study
- 1.5.1 General Objective
- 1.5.2 Specific Objectives
- 1.5.3 Research Questions
- 1.6 Research Methodology
- 1.6.1 Research Approach and Design
- 1.6.2 Evaluation of Research findings
- 1.6.3 Research Scope and Limitations
- 1.7 Significance of the Study
- 1.8 Layout of Thesis
- 1.9 Conclusion
- PART II: LITERATURE STUDY AND BACKGROUND RESEARCH
- Chapter 2 Research Related to Information Security in e-Government
- 2.1 Introduction
- 2.2 Information Security Requirements for e-Government
- 2.2.1 Security Requirements
- 2.2.2 Access Control
- 2.2.3 Security Management
- Chapter 3 Examples of Policy Level Information Security Frameworks
- 3.1 Introduction
- 3.2 Information Security Frameworks
- 3.2.1 Her Majesty’s Government (HMG) Security Policy Framework
- 3.2.2 Tasmania Government Information Security Framework
- 3.3 Interoperability Frameworks
- 3.3.1 South African Minimum Interoperability Standards (MIOS) for Information Systems in Government
- 3.3.2 Spanish National Interoperability Framework
- 3.4 Enterprise Architectures
- 3.4.1 Federal Enterprise Architecture Framework
- 3.4.2 Government Wide Enterprise Architecture
- 3.5 Conclusion
- Chapter 4 Standards Related to Information Security in e-Government
- 4.1 Introduction
- 4.2 Non – Technical Standards related to information security for G2G transactions
- 4.2.1 ISO/IEC 27001:
- 4.2.2 ISO/IEC 27002:
- 4.2.3 FIPS PUB
- 4.2.4 Network and Information Security Standards Report, Issue
- 4.2.5 OECD
- PART III: EAST AFRICAN COMMUNITY SITUATIONAL ANALYSIS
- Chapter 5 Current e-Government Initiatives and Practices in the EAC
- 5.1 Introduction
- 5.2 Regional EAC Initiatives
- 5.3 Initiatives in Rwanda
- 5.3.1 Resources
- 5.3.2 Government Policies, Strategies and Standards
- 5.3.3 Legal Environment
- 5.3.4 E-Government Implementations
- 5.3.5 National Cultural Considerations
- 5.4 Initiatives in Tanzania
- 5.4.1 Resources
- 5.4.2 Government Policies, Strategies and Standards
- 5.4.3 Legal Environment
- 5.4.4 e-Government Implementations
- 5.4.5 National Cultural Considerations
- 5.5 Initiatives in Uganda
- 5.5.1 Resources
- Chapter 6 Survey of Practices in Individual MDAs
- Chapter 7 Proposed Information Security Requirements for G2G Transactions in EAC
- Chapter 8 TOG Framework
- Chapter 9 Case Study
- Chapter 10 Evaluation of the TOG Framework
- PART V: CONCLUSION AND FUTURE WORK
- Chapter 11 Conclusions